Hopefully, I'm personally beyond that risk. At least I passed all the KnowBe4 classes I just took.
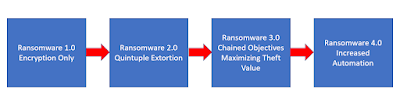
Recently KnowBe4's Roger Grimes posted an article on "Nuclear Ransomware 3.0."
We all know what ransomware started out doing.
He described Nuclear Ransomware 2.0 as "Quintuple Extortion."
The five elements were:
- Stealing Intellectual Property/Data
- Stealing Every Credential It Can - Business, Employee, Personal, Customer
- Threatening Victim’s Employees and Customers
- Using Stolen Data to Spear Phish Partners and Customers
- Publicly Shaming Victims
Those are bad enough.
Then he went on to suggest what Nuclear Ransomware 3.0 would consist of:
- Selling exfiltrated data
- Selling exfiltrated stolen credentials
- Selling initial access
- Stealing money from bank and stock accounts
- Personal extortion against individuals
- Hacking for hire
- Selling lead lists from stolen customer data
- Business email compromise scams
- Installing adware
- Launching DDoS attacks
- Crypto mining
- Creating rentable botnets
- Sending spam emails
- Resource renting
- Acting as proxy sites for other attacks
- Anything else they can think of to generate revenue
Yikes!
And some of these are already emerging. If you haven't heard of Initial Access Brokers (IABs), read this.
No comments:
Post a Comment