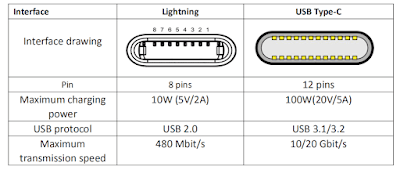
Years ago, a co-worker and I had a discussion about architecting our Unix systems as if each one was at risk from the network, even the LAN. His thinking was that you would never know where the threat was coming from so you should not trust anyone except those connections you made deliberately.
He was so far ahead of everyone else. And ahead of the technology available then.
Now we have
Software Defined Networking (SDN). Usually SDN is applied to Wide Area Networks (WANs). SDNs warrant a whole series of posts on their own.
This
excerpt from eSecurity Planet nails my co-worker's vision.
The Problem With Traditional Security Techniques
More traditional security tools, such as firewalls, VPNs and network access control (NAC), have their limits because they focus primarily on securing the network perimeter. Security teams historically assumed the biggest threats were attacking from outside the network. But that approach overlooked insider threats - and the damage that hackers could do when they eventually got inside the network.
SDN provides the underlying technology that wasn't available years ago.
But that allows you to worry about the next layer. What traffic do you allow
between systems? Now you need to get to
Layer 7 granularity.
Gardicore has a good
article that lays out the benefits (and challenges) of microsegmentation.
Benefits of Microsegmentation
Lateral Movement Security
Reduce Attack Surface
Secure Critical Applications
Then an organization has to consider the methods.
Microsegmentation by environment
Creating regulatory boundaries
Microsegmentation by application type
Microsegmentation by tier
The steps for an implementation effort are:
Identify what needs to be segmented
Tackle short-term goals
Deal with long term goals
Repeat
Labeling of assets is critical along with a comprehensive understanding of the applications relationships and dependencies.
I'll cover more of microsegmentation in future posts.